Why Zero Day Recovery is Essential to your Company’s Security
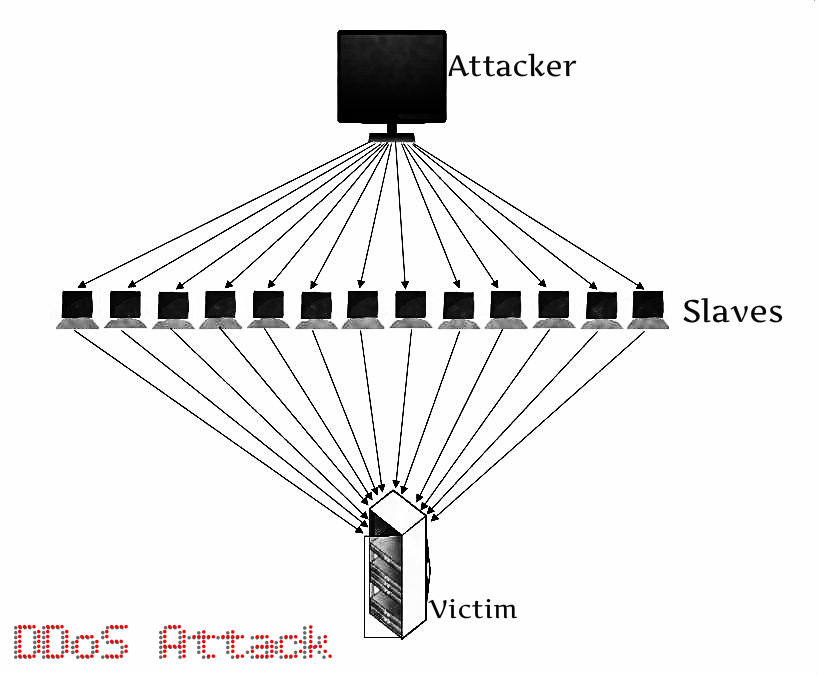
The Zero-Day-Recovery Cybersecurity Strategy One of the most immediate and adverse effects of a malware attack is the potential for the affected company to come to a complete productive halt. This is the case for all sorts of malware ranging from data-stealing Trojans to data-locking ransomware. Every moment that a company spends offline to deal…
Read more
Read more